Hardening OpenSSH using ssh-audit
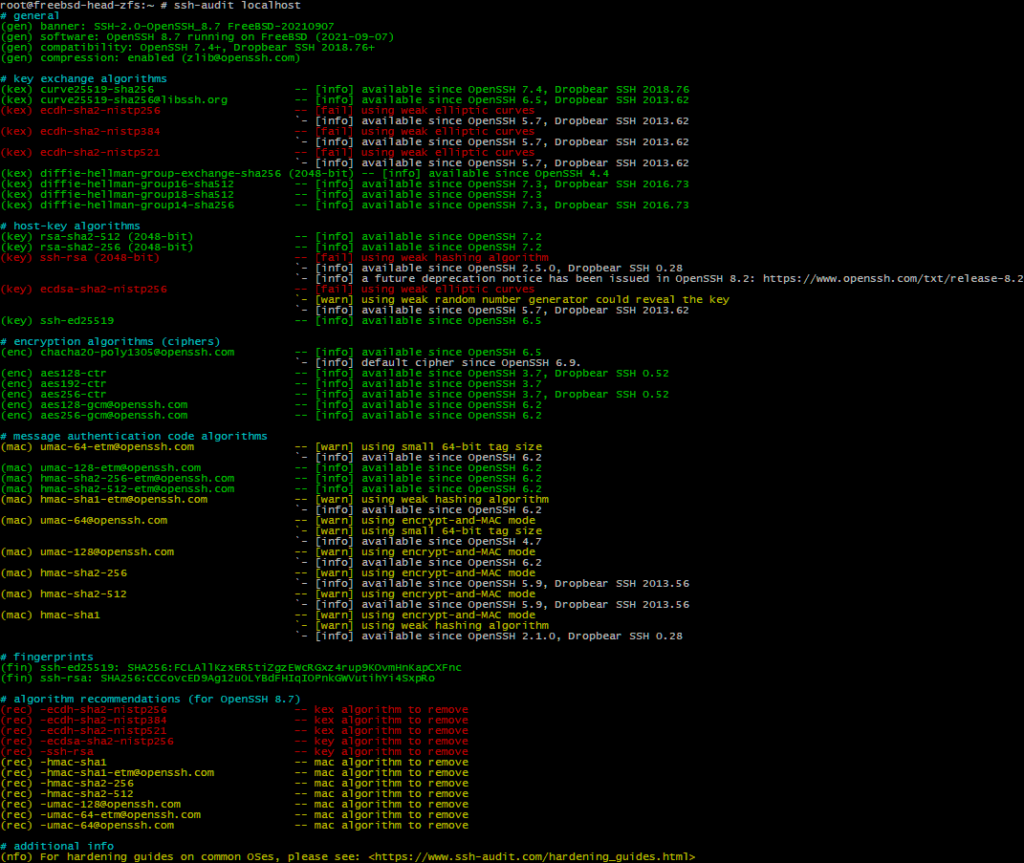
I recently came across security/py-ssh-audit@py38. Wielding this tool showed a lot to be improved.
Adding the four lines below to /etc/ssh/sshd_config, and preferably also to /etc/ssh/ssh_config, should make your OpenSSH on FreeBSD more suitable to the current threats. This should also be true for OpenSSH 8.7p1, recently added to FreeBSD ‑CURRENT.
Ciphers chacha20-poly1305@openssh.com,aes256-gcm@openssh.com,aes128-gcm@openssh.com,aes256-ctr,aes192-ctr,aes128-ctr HostKeyAlgorithms ssh-ed25519,rsa-sha2-512,rsa-sha2-256 KexAlgorithms curve25519-sha256,curve25519-sha256@libssh.org,diffie-hellman-group16-sha512,diffie-hellman-group18-sha512,diffie-hellman-group14-sha256,diffie-hellman-group-exchange-sha256 MACs hmac-sha2-256-etm@openssh.com,hmac-sha2-512-etm@openssh.com,umac-128-etm@openssh.com
Note, this configuration is only based what is recommended by the tool. Both it and myself could be dead wrong. You have been warned!
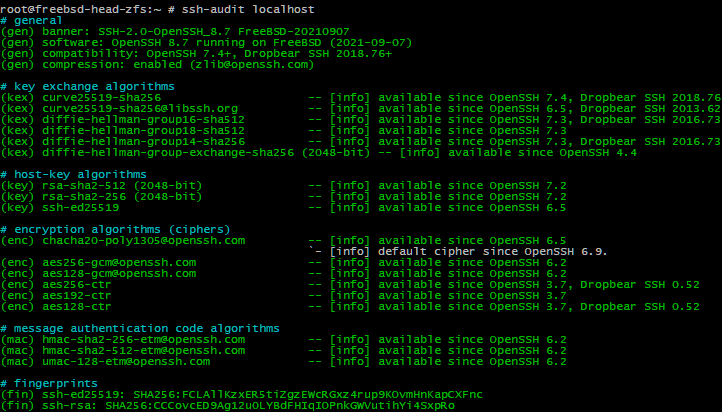
When using https://www.ssh-audit.com/ to scan a system using the “Hardened OpenSSH Server v8.5 (version 1)” policy, the KexAlgorithms line should read:
KexAlgorithms curve25519-sha256,curve25519-sha256@libssh.org,diffie-hellman-group16-sha512,diffie-hellman-group18-sha512,diffie-hellman-group-exchange-sha256
We are omitting diffie-hellman-group14-sha256.